Ensuring Automatic Tank Gauge Security Compliance
In today's interconnected world, ensuring the security of network-connected platforms is paramount. At Gilbarco Veeder-Root, we prioritize the security of our Automatic Tank Gauges (ATGs). Here’s how you can ensure your ATG systems remain secure and compliant.
Secure Your Console
The cornerstone of network security is placing your ATG behind a secure firewall. This practice is standard in most enterprise network environments, effectively mitigating known security threats. For independent or remote sites lacking a configured firewall, we recommend installing a basic firewall router.
Embrace PCI Compliance
While an ATG alone does not require PCI compliance, integrating proper security protocols can ensure it operates within a PCI-compliant network. To maintain compliance, best practices dictate placing the ATG on a separate network segment from payment processing devices. This segregation enhances security by minimizing potential vulnerabilities.
Set Up Safe Port Forwarding
When configuring port forwarding on your router to grant third-party access (e.g., to a fuel hauler or remote polling service), it is crucial to implement robust security controls. Limit access by configuring port forwarding with IP address restrictions and password protection to prevent unauthorized access.
Take Security to the Next Level
The TLS-450PLUS ATG, unlike its predecessors, was designed as an advanced network device from the outset, equipped with modern security features such as port management, network timing protocol, and secure socket layer communications. As security threats evolve, the TLS-450PLUS can leverage the latest software updates. Gilbarco Veeder-Root proactively releases frequent software releases to stay ahead of potential internet security concerns.
Customers seeking additional security on the TLS-450PLUS can take additional measures. Changing the default serial command port, adding password protection, or disabling the serial command port entirely via the Setup > System > Security menu. While this action blocks external traffic, it also restricts external monitoring services.
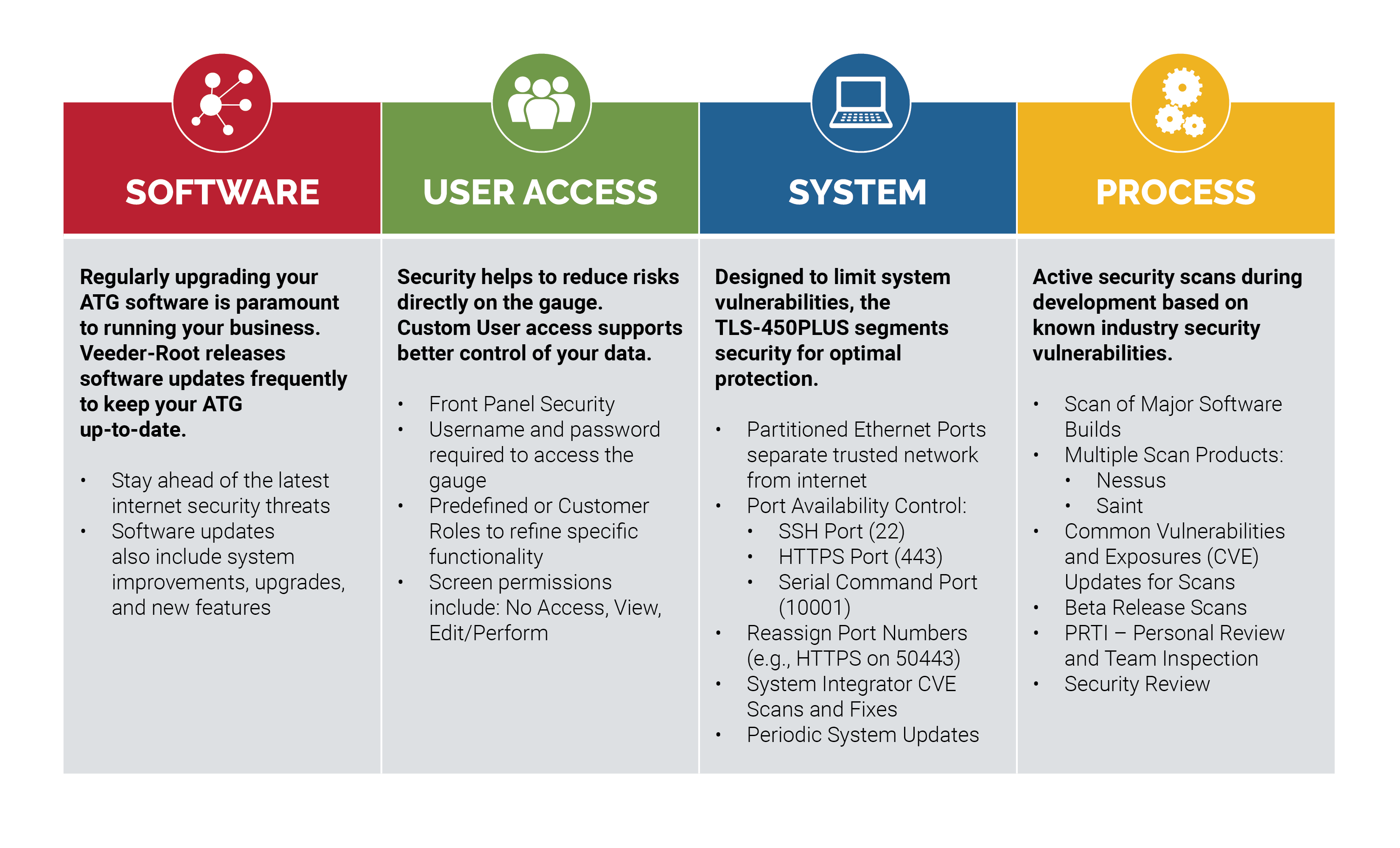
Follow the Four Pillars
At Gilbarco Veeder-Root, our approach to device security encompasses four pillars: software, user access, system, and process.
The Bottom Line
By adhering to these security measures, you can ensure your ATG systems remain secure, compliant, and resilient against potential threats.




